#100DaysOfCode
— san (@santoshpoojari3) August 19, 2021
Csharp Best practice - Const pic.twitter.com/bESVIrbfR3
Wednesday, August 18, 2021
Best Practice Csharp Use NameOf for Constant
Productivity Tool MSBUILDLog and Project
Download https://msbuildlog.com/
Visual Studio Build Log Extension
Tools to make working with the Visual Studio project system for C#, Visual Basic, and F# easier. This extension is for VS2017 and VS2019. Search the extension marketplace if you require a different version. Build loggingA tool window is added under See the docs for more information. |
https://marketplace.visualstudio.com/items?itemName=VisualStudioProductTeam.ProjectSystemTools
Monday, August 16, 2021
Hello world Csharp
Next time you write Hello World! Do this,
Saturday, June 5, 2021
Clean Code Exception Filters in c#
Clean code always looks like it was written by someone who cares.”
― Robert C. Martin, Uncle Bob
C# Exception filters has been around since advent of C# 6.0 , I'm sure we rarely use it because we are so used to old way of using conditional exception handling.
Cut to the chase........!
Run dotnet in browser
https://try.dot.net/


Happy Coding!
Sunday, May 30, 2021
Saturday, May 29, 2021
Azure Managed Identities- System Identity vs User Assigned Identity
Managed Identities
Managed Identities are in essence 100% identical in functionality and use case than Service Principals. In fact, they are actually Service Principals.
What makes them different though, is: – They are always linked to an Azure Resource, not to an application or 3rd party connector – They are automatically created for you, including the credentials; big benefit here is that no one knows the credentials
Managed Identities exist in 2 formats: – System assigned; in this scenario, the identity is linked to a single Azure Resource, eg a Virtual Machine, a Logic App, a Storage Account, Web App, Function,… so almost anything. Next, they also “live” with the Azure Resource, which means they get deleted when the Azure Resource gets deleted. – User Assigned Managed Identity, which means that you first have to create it as a stand-alone Azure resource by itself, after which it can be linked to multiple Azure Resources. An example here could be out of an integration with Key Vault, where different Workload services belonging to the same application stack, need to read out information from Key Vault. In this case, one could create a “read KV” Managed Identity, and link it to the web app, storage account, function, logic app,… all belonging to the same application architecture.
Let’s walk through a quick demo scenario for both, using a Virtual Machine as Azure Resource:
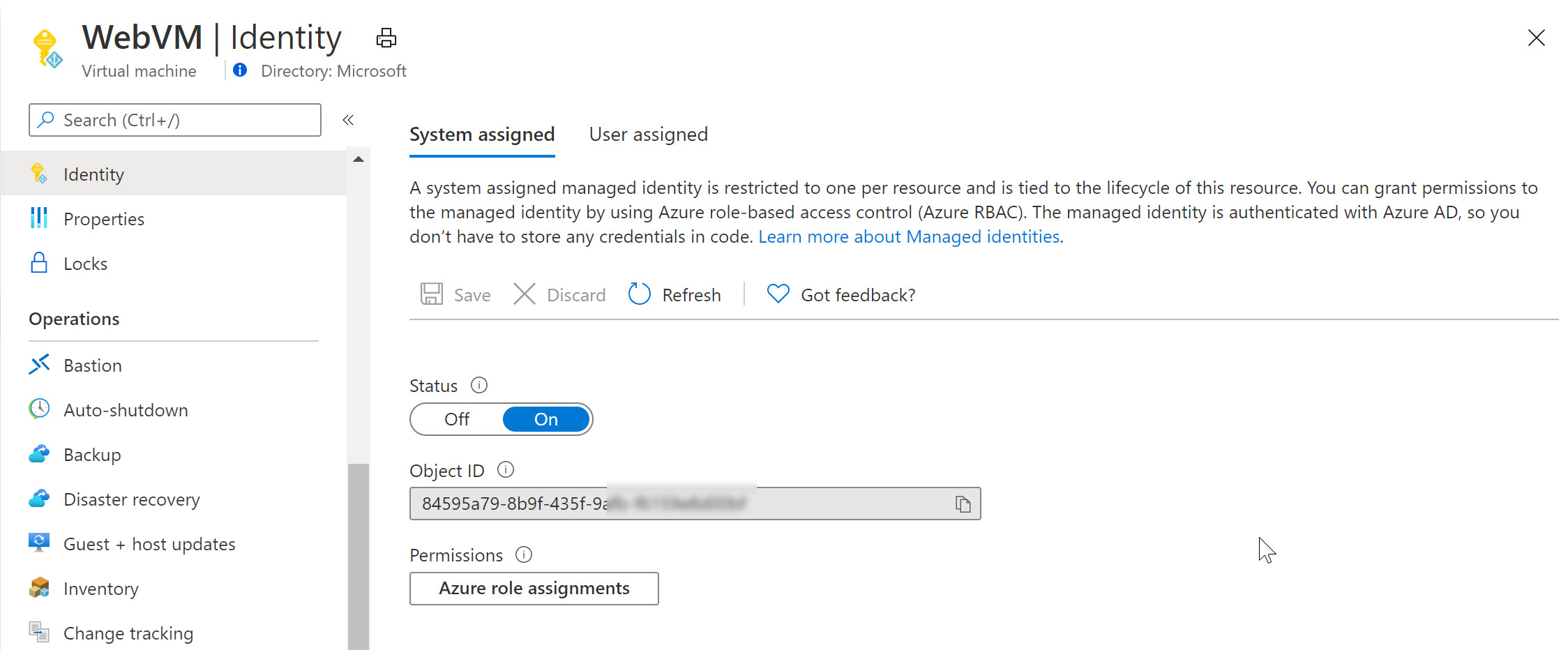
- From the Azure Portal, select the Virtual Machine; under settings, find Identity
- Set Status as On, and save the changes
Switching to Azure Key Vault / Access Policies, we can now define this System Assigned Managed Identity having get and list permissions (or any other) for keys, secrets or certificates. For example reading out an Azure Storage Account Access key or similar.
Notice how Azure Key Vault is expecting a Service Principal object here (where in reality we are using a Managed Identity).
Similarly, let’s remove the System Assigned MI of the VM and use a User Assigned one in the next example (an Azure Resource can only be linked to one or the other, not both…):
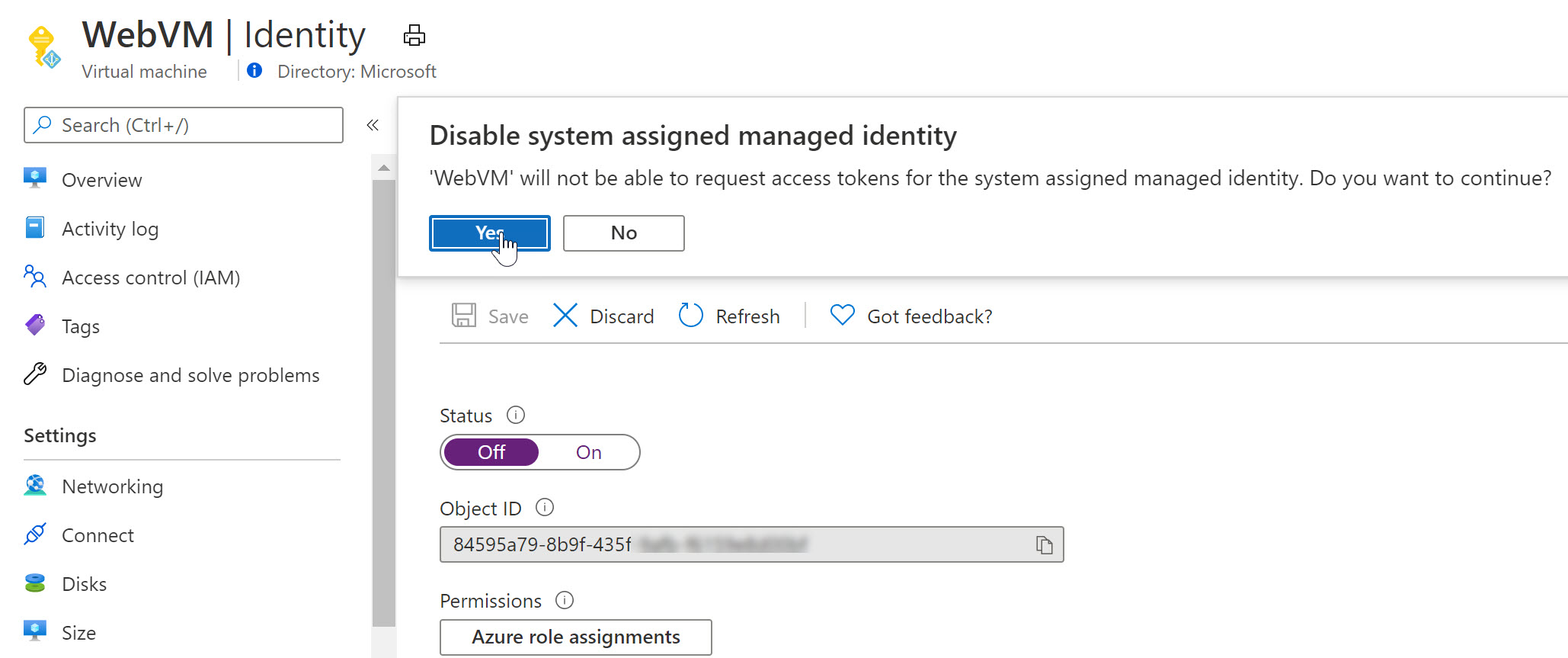
- From the Azure Virtual Machine blade, navigate to Identity and switch the “Status” toggle button to Off.
- This will prompt for your confirmation when saving the settings
As you notice, the Managed Identity object gets immediately removed from Azure AD. Yes, security is key here…
- Wait for the deregistration of the object.
Remember that a User Assigned Managed Identity is a stand-alone Azure Resource, which needs to be created first, after which you can assign it to another Azure Resource (our VM in this scenario).
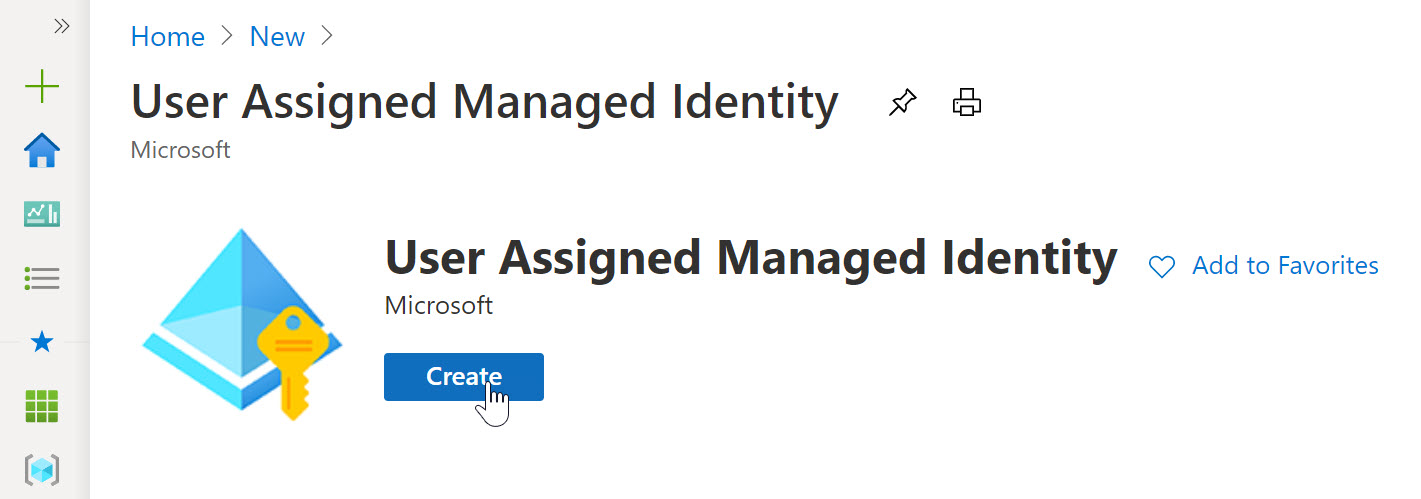
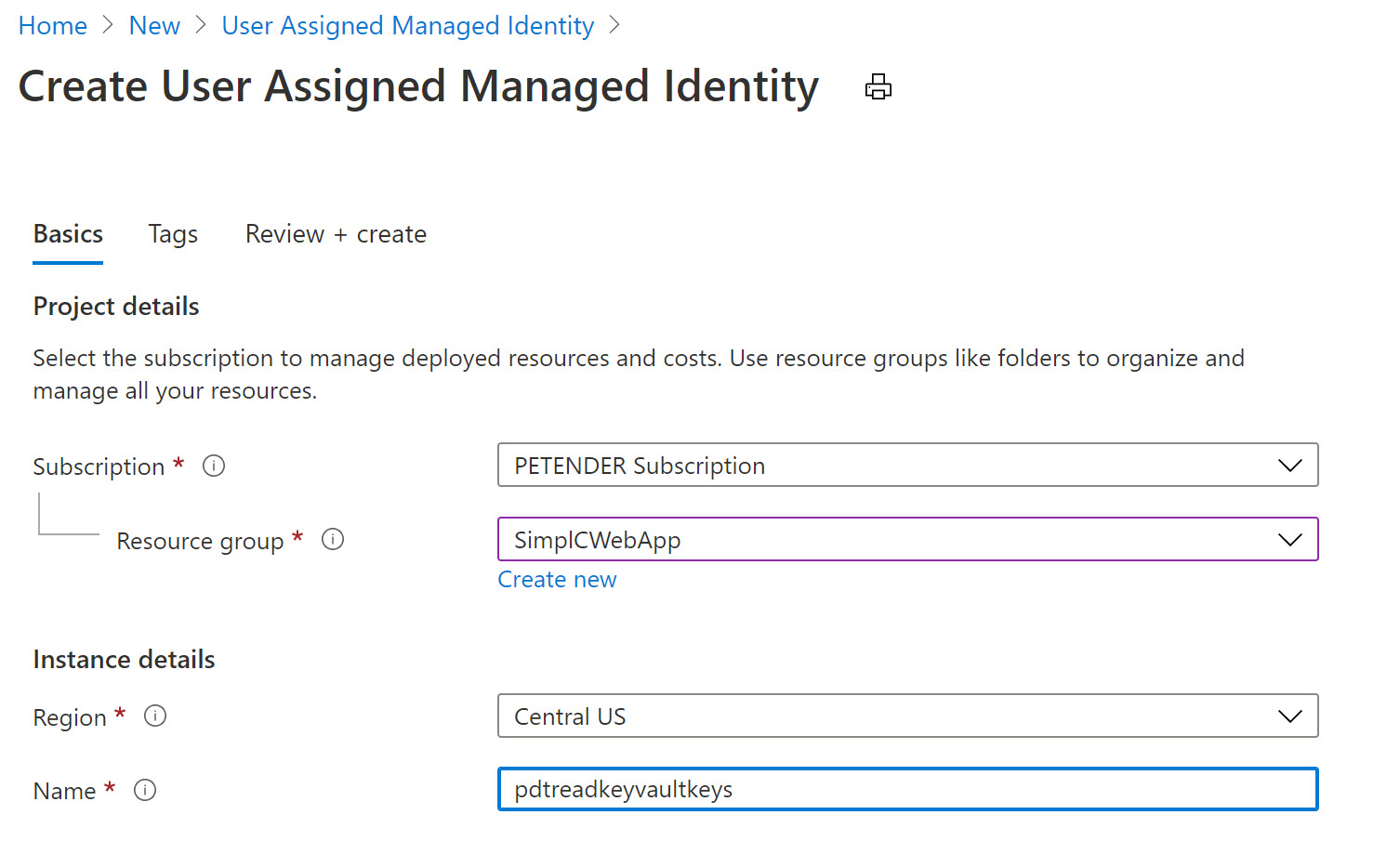
- From the Azure Portal, Create new Resource, and search for “User Assigned Managed Identity”
- click Create.
- Specify the Resource Group, Azure Region and Name for this resource.
- Confirm by clicking create and Wait for the resource creation to complete successfully.
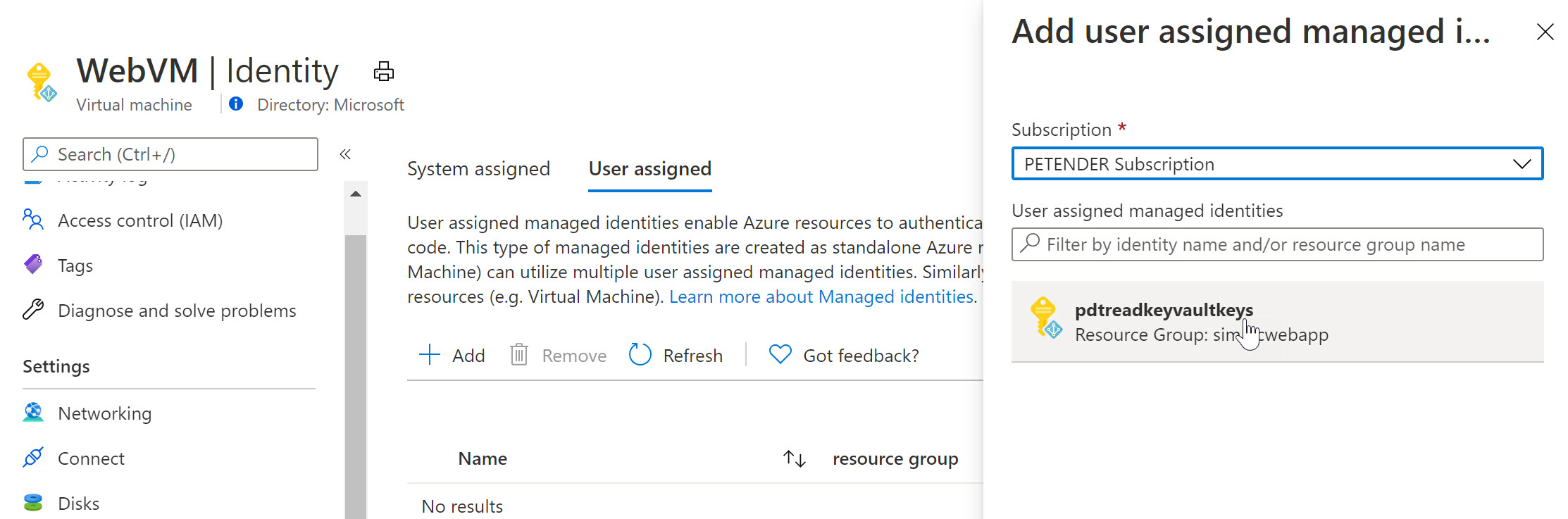
- Once created, switch back to the Azure Virtual Machine, select Identity and select User Assigned
- Notice the Managed Identity you just created.
Select it and add it as a Virtual Machine User Assigned object.
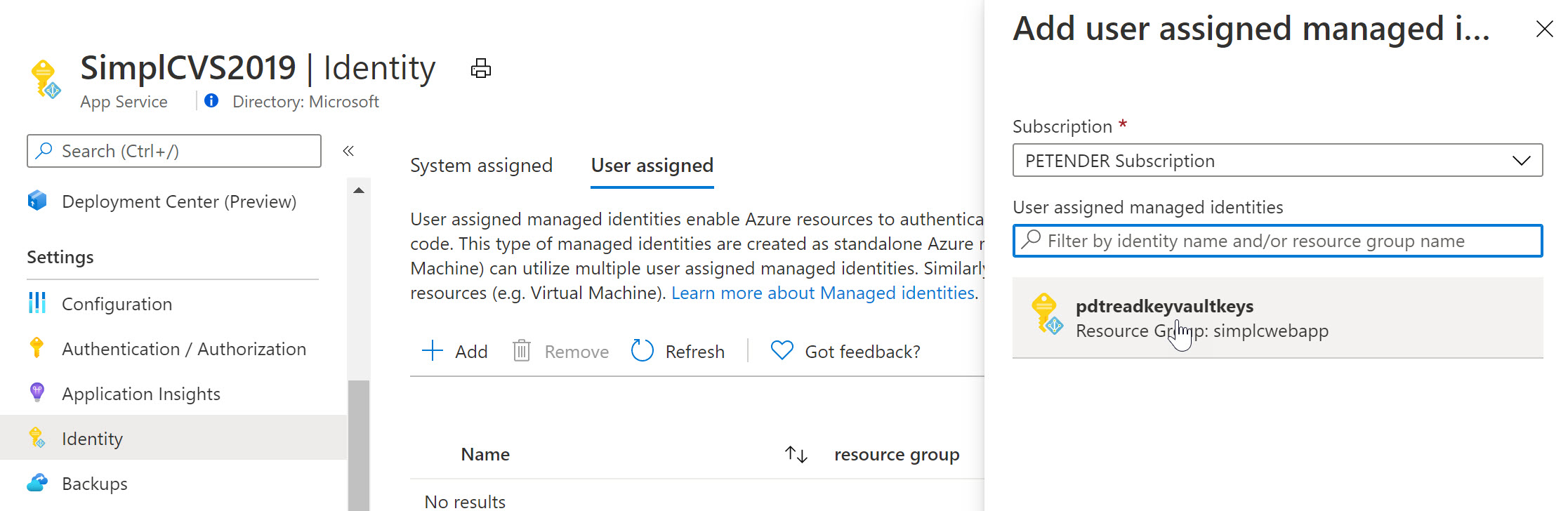
Select another Azure Resource in your subscription, for example an Azure Web App, Logic App,… and once more select Identity from the settings. Below screenshot shows what it looks like for an Azure Web App Resource:
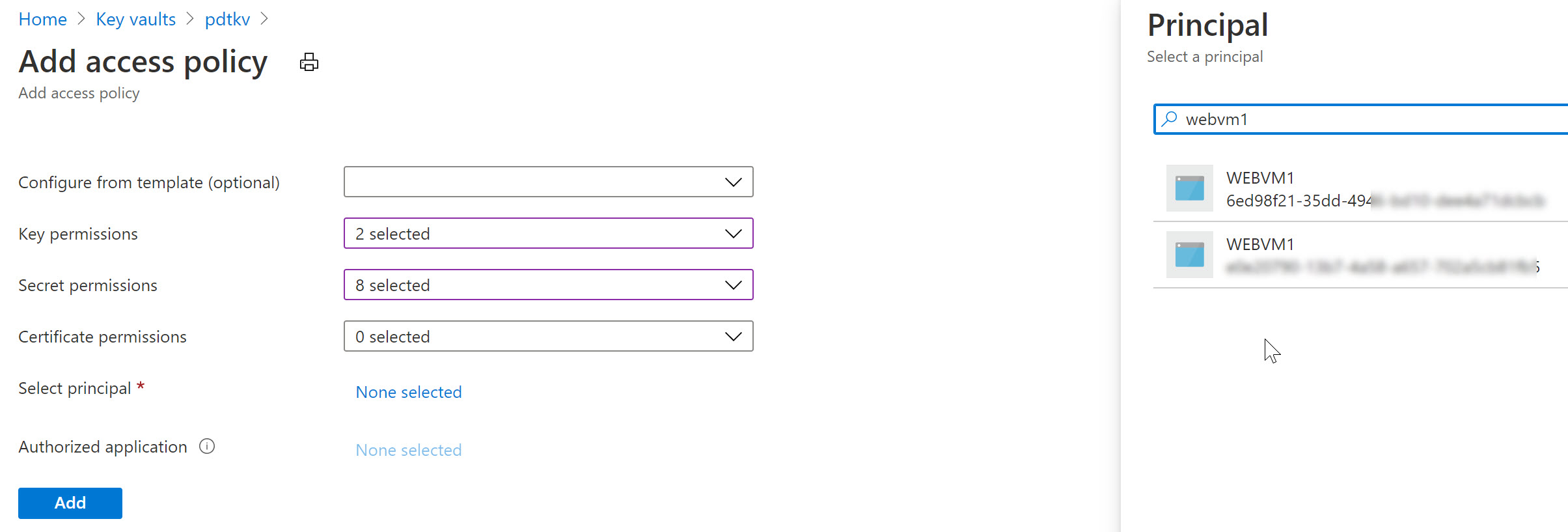
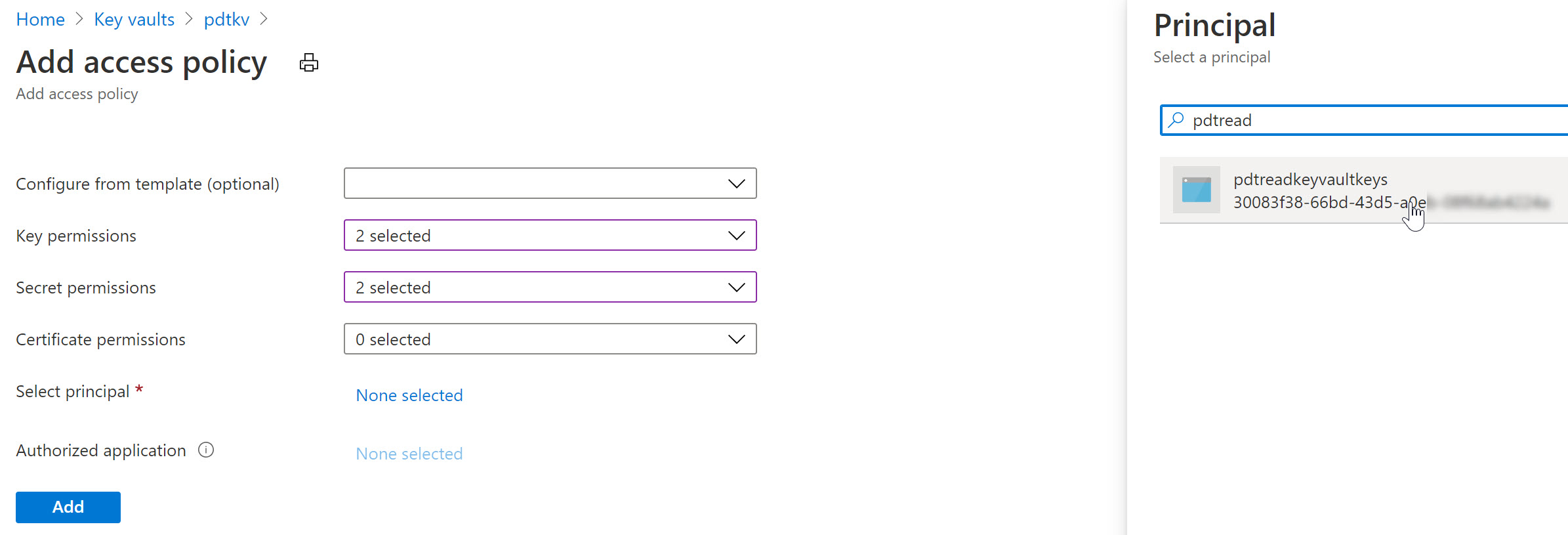
To complete the sample scenario, let’s go back to Azure Key Vault, and specify another Access Policy for this User Assigned Managed Identity:
- Select your Azure Key Vault resource, followed by selecting Access Policy from the settings.
- Specify the Key and/or Secret Permissions (for example get, list)
- Click “Select Principal” and search for the User Assigned Managed Identity you created earlier
After saving the changes, the result is that now both the Azure Virtual Machine as well as the Web App – having the User Assigned Managed Identity assigned to them – can read our keys and secrets from Azure Key Vault.
Summary
In this post, I wanted to clarify the use case, difference and similarities between Service Principals and Managed Identities. A Service Principal could be looked at as similar to a service account-alike in a more traditional on-premises application or service scenario. Managed Identities are used for “linking” a Service Principal security object to an Azure Resource like a Virtual Machine, Web App, Logic App or similar. For a 1:1 relation between both, you would use a System Assigned, where for a 1:multi relation, you would use a User Assigned Managed Identity.
Azure messaging services - Event Grid, Event Hubs, and Service Bus
Comparison of services
| Service | Purpose | Type | When to use |
|---|---|---|---|
| Event Grid | Reactive programming | Event distribution (discrete) | React to status changes |
| Event Hubs | Big data pipeline | Event streaming (series) | Telemetry and distributed data streaming |
| Service Bus | High-value enterprise messaging | Message | Order processing and financial transactions |
Wednesday, May 26, 2021
Azure Traffic Manager , WAF CDN , DNS -Load Balancer
Client Browser--> DNS Lookup---> WAF/CDN---> Azure Traffic manager--> Main Site URL and DR (Disaster Recovery URL)
Tuesday, April 27, 2021
Cool Stuff Microsoft Math Solver in Microsoft EDGE browse
Go to the three dotted , click on it then select Apps-> Manage App
On the Edge Search Bar ,S type in Flags , see the screenshot for more details.

It is experiments package, so Click on ENABLED and then on Restart button to initiate and installation of this app.
Saturday, April 24, 2021
Web Developer must know -File Sharing Protocol Filesystem- NFS, SMB, AFP and FTP
File sharing protocols: Application Layer |
|
|
Protocol |
Description |
|
SMB (Server Message Block) |
Supported by Microsoft Windows computers and sometimes by Mac OS X protocol
is enabled by default. It is sometimes referred to as the CIFS (Common
Internet File Service) file-sharing protocol. SMB uses TCP/IP. |
|
NFS (Network File Service) |
Linux and Unix computers use NFS. Mac OS X users can access NFS shared
folders through console shell access. UDP and TCP and NFS v4 over TCP. |
|
AFP (Apple File Protocol) |
Mac OS X computers use AFP. |
|
FTP (File Transfer Protocol) and FTPS (FTP with
SSL encryption) |
Many public file upload and download sites use FTP. |
|
Rsync |
Fast file-transfer protocol that uses a delta-transfer algorithm that
sends only the differences between the source file and the existing file. |
|
HTTP (Hypertext Transfer Protocol and HTTPS (HTTP
with SSL encryption) |
Used on the World Wide Web. |
|
SSH( Secure Socket Shell |
Remote access to machine vis SSH connection. |
Sunday, April 11, 2021
Tuesday, March 30, 2021
Thursday, March 25, 2021
Latency vs Bandwidth vs Throughput
We come across these terms Latency, Bandwidth and throughput. Sometimes we might have confused ourselves most of the time. Below images are thousand words.
Sunday, March 21, 2021
Thursday, March 18, 2021
Was SSL now it is TLS
HTTP

HTTPS

SSL

SSL 1.0
SSL 2.0
SSl 3.0
SSL 3.1
Netscape Navigator Browser :SSL 1.0/2.0



History Browser War
{ IE vs Netscape }
In the year 1999 Browser War erupts between Microsoft IE and Netscape Navigator Browser .
Many developers had no choice but to tailor their websites for one browser or the other. Of course, it was ultimately the users that suffered.
With the release of Internet Explorer 3.0, Microsoft dropped the hammer. They included this version, for free, bundled right into the Windows ’95 operating system.
Netscape pricing model fell apart
In November of 1998, Netscape was sold to AOL for $4.2 billion- The end of pioneer.

TLS : Awakening of TLS


Some known facts, 10% of the time ,On prim application downtime is due to expired certificate.