Recently we have encountered some unusual behavior when customer tries to login using Azure B2C authentication framework.
|
Application Type |
Web |
|
Technology |
.Net
Framework 4.8 Asp.net MVC |
|
CMS |
Sitecore CMS 10.0.0 |
|
Authentication Framework |
Azure B2C .Net MSAL Open Id connect |
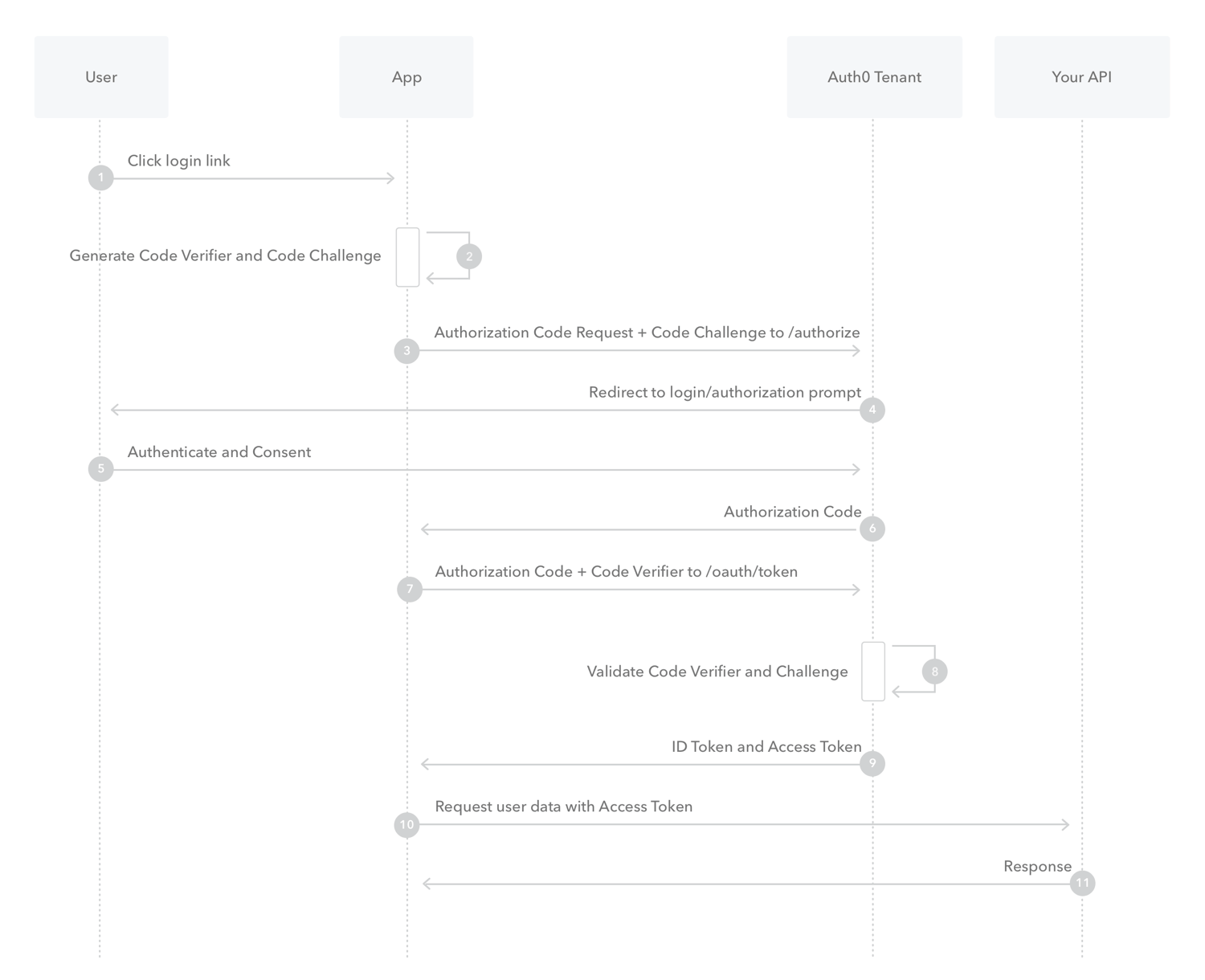
Problem Statement:
User idle for 15 mins and user taken back to Website Sign In page to initiate login again.
Root Cause: Token Exchange Failure. Nonce and Codeverifier expires after 15 mins. User Idle on sign In Page for more than 15mins and post that enters credential and results in login loop.
https://learn.microsoft.com/en-us/azure/active-directory-b2c/authorization-code-flow
Issue reported to Microsoft
Solution: Increase Nonce and Codeverifier expiry timeout.


No comments :
Post a Comment